Introduction to Public Key Cryptography in GRIDNET
Notice: Many GRIDNET OS GridScript commands come with built-in MAN pages. The MAN page of the main utility described herein is available through
keychain -help

Public key cryptography forms the foundation of security in GRIDNET’s decentralized operating system. To understand how GRIDNET manages identities and secures assets, let’s first explore the core concepts of public key cryptography.
Core Concepts

At its heart, public key cryptography uses a pair of mathematically related keys: a private key and a public key. In GRIDNET, these keys are generated using Elliptic Curve cryptography, which provides strong security while keeping key sizes manageable. Here’s how the system works:
Private Keys
- A private key is a secure, randomly generated number that must be kept strictly confidential
- Think of it as your digital master key or signature
- In GRIDNET, this is what you see as your “Secret” in the mobile app
- Anyone who has your private key can control your State Domains (accounts) and assets
- Private keys should never be shared or stored in unsecured locations
Public Keys
- Each private key has a corresponding public key that’s mathematically derived from it
- The public key can be freely shared without compromising security
- It’s computationally infeasible to determine the private key from the public key
- In GRIDNET, your public key is used to derive your State Domain addresses
Addresses
In GRIDNET, your public-facing identity (address) is derived from your public key through a series of cryptographic operations. This creates a human-readable format that’s easier to work with than raw public keys. Think of your address as your account number that others can use to interact with your State Domain.
Digital Signatures and Authentication
GRIDNET OS State Domains and authentication are brought to next level due to innovative authentication model. Imagine you are using a decentralized graphical application hosted atop of GRIDNET OS. The application is a decentralized streaming service delivering movies frames to you while every now and then displaying a QR code indicating the service provider (the remote app) requires an off-the-chain payment. You pull out your mobile app scan the QR code and everything happens under the hood through an onion routed connection. The remote app is notified and so is the decentralized user interface visibile in your web browser.

When you perform operations in GRIDNET, such as sending tokens or interacting with smart contracts, here’s what happens behind the scenes:
- The operation details are combined into a message
- Your private key creates a unique digital signature for this message
- Anyone can verify this signature using your public key
- The signature proves you authorized the operation without revealing your private key

This system ensures that:
- Only you can create valid signatures for your State Domain
- Others can verify your signatures without knowing your private key
- Signatures cannot be forged without access to the private key
- Each signature is unique to the specific operation being performed

The GRIDNET Innovation: Multi-dimensional Keys
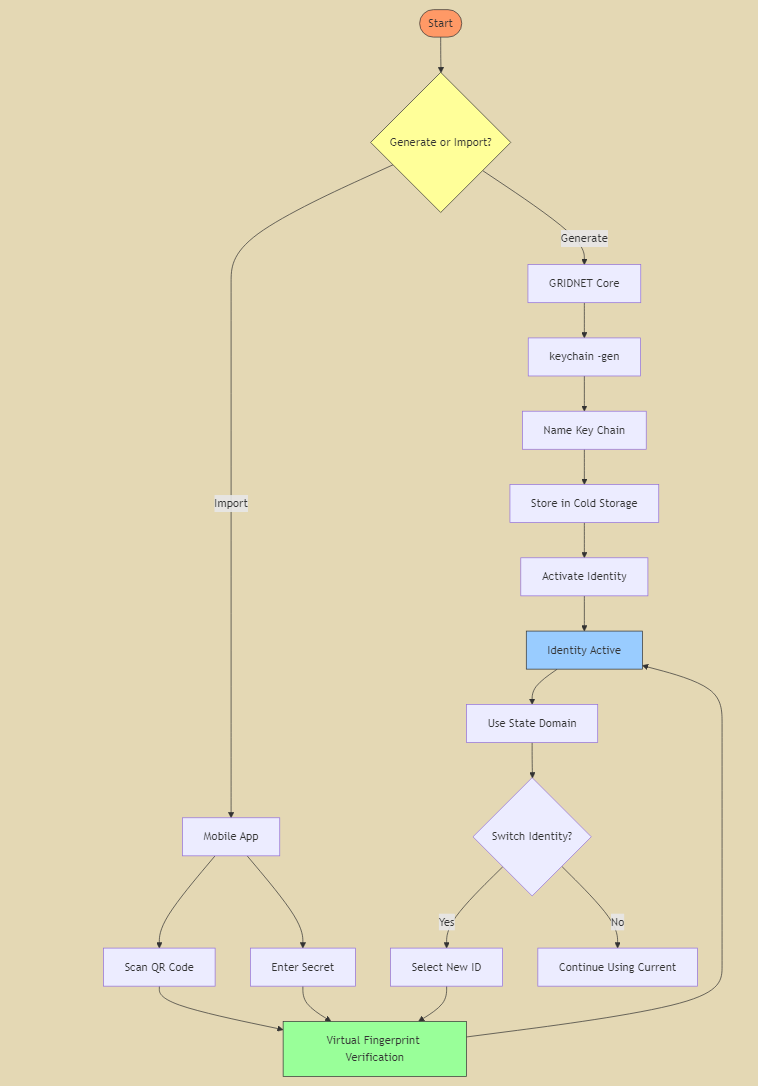
GRIDNET introduces an innovative, in terms of interactive (also supporting autonomous identity switching during mining Operations!) command line management , approach to key management through its multi-dimensional key system:
Flat Keys
- Traditional single-purpose private keys
- Each key controls exactly one State Domain
- Simpler to understand but less flexible for managing multiple accounts
Multi-dimensional Keys (Master Private Keys)

- Can control multiple State Domains from a single master key
- Uses a clever “Vector IV” system to derive sub-identities
- More efficient for users managing multiple accounts
- Built-in support in both GRIDNET Core and Mobile app

This multi-dimensional approach offers several advantages:
- Simplified backup (just one master key to secure)
- Easy management of multiple identities
- Seamless switching between different State Domains
- Enhanced security through compartmentalization
Security Implications
Understanding public key cryptography helps you appreciate why:
- Private keys must be backed up securely
- Never share your private key or “Secret” with anyone
- Export operations should be performed in secure environments
- Different State Domains can be isolated while still being controlled by one master key
- The importance of the fingerprint verification in the mobile app
In the following sections, we’ll explore how to practically manage these cryptographic elements using both GRIDNET Mobile and Core, but this fundamental understanding of public key cryptography will help you make informed decisions about key management and security.
Next, we’ll dive into how GRIDNET implements these concepts in its identity system, building on this cryptographic foundation to create a flexible and secure decentralized operating system.
GRIDNET Identity System Overview
State Domains: The Foundation of GRIDNET Identity
In GRIDNET’s decentralized operating system, a State Domain functions as what we traditionally think of as an account or wallet. However, it’s more sophisticated than traditional cryptocurrency wallets, as it represents a complete computational environment within the decentralized OS. User may use these State Domain to host decentralized applications, also graphical ones, apps that can be interacted with in real-time, decentralized websites, use these for real-time off the chain transactions and so much more!
State Domains have several key characteristics:
- Each has a unique address derived from a public key
- Can hold tokens and other digital assets
- Functions as a complete operating environment
- Can interact with other State Domains
- Requires cryptographic authorization for operations
The Two-Tier Key Architecture
GRIDNET implements an innovative two-tier approach to key management:
Flat Keys (Single-Dimensional)
- Traditional one-to-one relationship
- One private key → one State Domain
- Simpler to understand and manage
- Ideal for single-purpose accounts
- Limited flexibility for managing multiple domains
Master Private Keys (Multi-Dimensional)
- One master key → many State Domains
- Uses Vector IV system for sub-identity derivation
- More efficient for managing multiple domains
- Built-in support in both Core and Mobile
- Enhanced backup efficiency
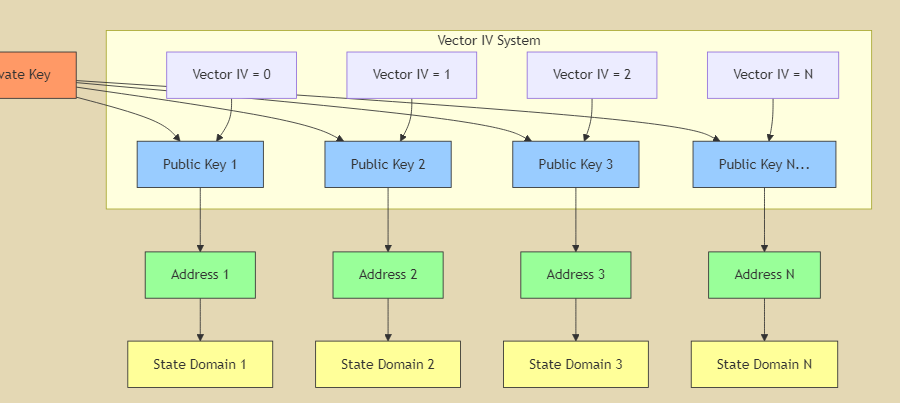
Understanding Vector IV and Sub-Identities
The Vector IV system is what makes GRIDNET’s multi-dimensional keys possible. Here’s how it works:
- Master Key Generation
- A secure random master private key is generated
- This becomes the root of all sub-identities
- Sub-Identity Derivation
- Each sub-identity is derived using the Vector IV value
- Vector IV starts at 0 and can be incremented
- Mathematical formula: Sub-Identity Private Key = Master Private Key + Vector IV
- Each increment creates a new, unique sub-identity
- Key Properties
- All sub-identities are deterministic
- Can be reconstructed from master key
- Each has its own unique address
- Completely isolated from other sub-identities
Example using the keychain utility:
# Generate a new master key chain keychain -gen -name masterchain1 # Create first sub-identity (Vector IV = 0) keychain -activate -id 0 # Create next sub-identity (Vector IV = 1) keychain -genid
Identity Management in Practice
In GRIDNET Core
Core users (typically miners) can manage identities through the keychain utility:
- Generate new key chains
- Store keys in cold storage
- Export keys in various formats
- Manage multiple sub-identities
- Switch between active identities
Example of managing identities in Core:
# Show current identity information keychain -show # Switch to a different sub-identity keychain -activate -id 2 # Export master key for backup keychain -export -master # Generate QR code for mobile import keychain -export -qr
In GRIDNET Mobile
Mobile app users have a streamlined interface:
- Single master key storage
- Simple identity switching
- Fingerprint security
- QR code import support
- Automatic address generation
Navigation:
- Tap settings wheel (bottom right)
- Access Secret field for key management
- Use fingerprint scanner for security
- Toggle between sub-identities as needed
Identity Isolation and Security
Each sub-identity, despite coming from the same master key, operates as a completely isolated environment:
- Separate address
- Independent balance
- Distinct transaction history
- Isolated computational state
- Individual access controls
This provides several benefits:
- Compartmentalization of assets
- Risk management
- Privacy enhancement
- Organizational flexibility
Practical Applications
- Mining Operations
- Separate mining identity
- Isolated mining rewards
- Independent operational control
- Personal Finance
- Different identities for different purposes
- Easy switching between accounts
- Unified backup through master key
- Business Operations
- Segregated business accounts
- Clear operational boundaries
- Simplified key management
- Development and Testing
- Isolated test environments
- Easy creation of new identities
- No risk to main accounts
Best Practices for Identity Management
- Always backup master keys
- Use meaningful key chain names in Core
- Document sub-identity purposes
- Regularly verify active identities
- Use fingerprint security in mobile
- Export keys in secure environments
- Maintain clear identity organization
GRIDNET Mobile App Key Management
Overview
GRIDNET’s mobile app provides a user-friendly interface for managing both flat and multi-dimensional keys while maintaining robust security. This section explores the complete key management functionality available in the mobile application.

Default Key Generation
When you first launch the GRIDNET mobile app, it automatically generates a Master Private Key (multi-dimensional key). This approach provides several advantages:
- Single key backup requirement
- Built-in support for multiple identities
- Seamless identity switching
- Future-proof key management
Navigating the Settings View
To access key management features:
- Locate the settings wheel icon in the bottom right corner
- Tap to open the Settings view
- The “Secret” field appears at the top
- Additional controls become available after key activation
Understanding the Secret Field
The Secret field is your gateway to key management:
- Displays your active private key
- Accepts both flat and master private keys
- Automatically derives public keys
- Generates corresponding addresses
- Supports manual key entry and QR scanning
Identity Activation Process
- Key Entry
- Enter private key in Secret field
- Or scan QR code from GRIDNET Core
# Generate QR in Core for scanning keychain -export -qr
- Fingerprint Verification
- Virtual Fingerprint Scanner appears
- Touch to confirm identity activation
- Provides additional security layer
- Prevents accidental identity changes
- Automatic Processing
- Public key generation
- Address derivation
- Balance checking
- Sub-identity detection
Managing Multiple Identities
Once a master key is activated, the app provides tools for managing sub-identities:
Identity Switching
- Additional controls appear after activation
- Seamlessly toggle between sub-identities
- Real-time balance updates
- Automatic address switching
Sub-Identity Controls
- Identity Index: [0] [1] [2] [3]
- Current Address
- Current Public Key
Identity Tracking
- Each sub-identity maintains:
- Unique address
- Independent balance
- Separate transaction history
- Individual settings
Importing Keys
The mobile app supports two key import methods:
QR Code Import
- From GRIDNET Core:
# Export master key as QR keychain -export -master -qr # Export specific sub-identity keychain -export -id 2 -qr
- In mobile app:
- Tap QR scanner icon
- Center QR code in viewport
- Automatic key detection
- Fingerprint verification required
Manual Text Import
- From GRIDNET Core:
# Export master key as text keychain -export -master # Export specific sub-identity keychain -export -id 2
- In mobile app:
- Copy key to Secret field
- Verify fingerprint
- Automatic activation
Backup Recommendations
The mobile app supports robust key backup strategies:
Essential Backup Practices
- Master Key Backup
- Export master key from Settings
- Store in secure location
- Consider multiple backup copies
- Use offline storage when possible
- Sub-Identity Documentation
- Record active identity indices
- Document identity purposes
- Maintain usage records
- Keep backups updated
Security Considerations
- Never share your Secret
- Use secure channels for key transfer
- Enable device security features
- Regular backup verification
- Consider cold storage solutions
Common Operations
Checking Active Identity
- Open Settings
- View current Secret
- Note identity index
- Verify address
Switching Identities
- Access Settings
- Use identity toggles
- Confirm with fingerprint
- Verify new address
Creating New Sub-Identity
- Navigate to Settings
- Select next available index
- Verify with fingerprint
- Document new identity
Troubleshooting
Common issues and solutions:
- Invalid Key Format
- Verify key format
- Check for copy errors
- Try QR import instead
- Failed Activation
- Retry fingerprint scan
- Check key validity
- Restart app if needed
- Balance Issues
- Verify correct identity
- Check network connection
- Allow sync completion
Best Practices
- Regular Backups
- Export master key periodically
- Store backups securely
- Test backup restoration
- Identity Organization
- Label sub-identities
- Document usage
- Regular verification
- Security Habits
- Regular fingerprint checks
- Secure app access
- Private key confidentiality
GRIDNET Core Key Management
Introduction to the KeyChain Utility
The keychain utility in GRIDNET Core is the primary tool for managing cryptographic identities. It provides comprehensive functionality for handling both flat and multi-dimensional keys, with powerful features for miners and advanced users.
Core Concepts and Operations
Key Storage Architecture
GRIDNET Core implements a two-tier storage system:
- Active Memory (Ephemeral State)
- Currently loaded keys
- Active identities
- Runtime configurations
- Cold Storage (Persistent State)
- Saved key chains
- Long-term storage
- Backup configurations
Basic Key Management Commands
Generating New Key Chains
# Generate with auto-assigned name keychain -gen # Generate with custom name keychain -gen -name mining_master # Generate and immediately store keychain -gen -name mining_master -store
Viewing Key Information
# Show current key chain keychain -show # Show including private key keychain -show -priv # Show specific key chain keychain -show -name mining_master
Managing Multiple Key Chains
Storage Operations
# Store current key chain keychain -store # Store with new name keychain -store -name backup_chain # Store specific identity keychain -store -id 2 -name mining_backup
Activation Operations
# Activate stored key chain keychain -activate -name mining_master # Activate specific sub-identity keychain -activate -id 2 # Generate and activate new sub-identity keychain -genid -activate
Advanced Features
Sub-Identity Management
# List all sub-identities keychain -show # Generate next available identity keychain -genid # Switch to specific identity keychain -id 3 -activate # Export specific sub-identity keychain -export -id 2
Export Operations
Text-Based Export
# Export master key keychain -export -master # Export current sub-identity keychain -export # Export named key chain keychain -export -name backup_chain
QR Code Export
# Export master key as QR keychain -export -master -qr # Export sub-identity as QR keychain -export -id 2 -qr # Export with custom name included keychain -export -qr -named
Key Chain Naming Conventions
GRIDNET Core uses a structured naming system:
- Default format:
keyX(where X is an incremental number) - Custom names: up to 20 alphanumeric characters
- Case-sensitive
- No special characters allowed
Examples:
# Default names key0, key1, key2 # Custom names mining_master validator_backup test_chain
Practical Workflows
Setting Up Mining Identity
# Generate new key chain keychain -gen -name mining_master # Store it keychain -store # Activate for mining keychain -activate # Verify active identity keychain -show
Managing Multiple Mining Identities
# Generate new sub-identity keychain -genid # Activate it keychain -activate -id 1 # Export for backup keychain -export -master -name mining_backup
Mobile Integration
# Export to mobile (QR) keychain -export -master -qr # Export specific identity (QR) keychain -export -id 2 -qr # Export text format keychain -export -master
Security Considerations
Private Key Protection
- Use
-privflag carefully - Secure environment for exports
- Regular backup procedures
- Cold storage best practices
Identity Isolation
- Separate mining identities
- Different chains for different purposes
- Regular verification of active identity
- Clear documentation
Troubleshooting Common Issues
First of all worry not. Assets or your account can never disappear just like that. That is impossible. As long as you keep your private keys secure.
Below we outline a couple of methodologies for investigating things and moving around. In short, in GRIDNET OS your ‘wallet’ is a true ‘account’ on a decentralized operating system GRIDNET OS. Which mean you can CD into your account just as you would on Linux , MacOS, DOS or Windows.
First you may want to execute the whoami GridScript command to see if it corresponds to the identity you’ve activated with keychain:

whoami would report all sub-identities associated with your active key-chain along with all corresponding assets, including locked ones. Notce that currently active sub-identity is clearly depicted. That’s the identity which is currently being used for mining/Operating purposes.
Next, you may try to CD into your account, just like so:

Notice that GRIDNET OS automatically attempts to associate current State Domain with one of private keys available in your currently active key-chain. Here it reports having successfully found a corresponding private key at position 0 in your active Key Chain.
If on the other hand you attempt CDing into someone else’s account:

That means Core was unable to find a private sub-key which would match the currently active domain. Probably you’ve imported an invalid Mater Private Key or haven’t activated the proper key-chain.
- Key Chain Not Found
# Verify existence keychain -show -name missing_chain # List available chains keychain -show
- Invalid Operations
# Check active chain keychain -show # Verify permissions keychain -store
- Export Issues
# Verify key chain status keychain -show # Try alternative export format keychain -export -master
Best Practices
- Regular Maintenance
- Document all key chains
- Regular backup exports
- Verify active identities
- Clean up unused chains
- Security Protocols
- Secure export environment
- Regular permission checks
- Backup verification
- Access control
- Organization
- Consistent naming
- Clear documentation
- Regular audits
- Version control
Practical Scenarios with Examples
A. Generating New Keys
Creating New Key Chains
The process of generating new keys in GRIDNET can be done through both Core and Mobile app. Let’s explore each method:
In GRIDNET Core
# Basic key generation keychain -gen # Named key generation keychain -gen -name mining_main # Generate, store, and activate in one command keychain -gen -name mining_main -store -activate
In GRIDNET Mobile
- Clear the Secret field in Settings
- Let the app auto-generate a new master key
- Confirm with fingerprint
- Back up the generated key immediately
Naming Conventions
GRIDNET follows specific naming rules for key chains:
# Standard auto-generated format key0, key1, key2... # Recommended naming patterns mining_[purpose] # e.g., mining_main, mining_backup validator_[role] # e.g., validator_primary test_[purpose] # e.g., test_development
Best Practices for Names:
- Maximum 20 characters
- Alphanumeric only
- Use underscores for readability
- Include purpose in name
- Be consistent across chains
Storage and Activation
# Store newly generated key keychain -store -name mining_primary # Verify storage success keychain -show -name mining_primary # Activate stored key keychain -activate -name mining_primary # Verify active status keychain -show
B. Managing Multiple Identities
Generating Sub-identities
# Generate next available sub-identity keychain -genid # Generate and activate specific index keychain -genid -id 3 -activate # Verify new identity keychain -show
Example workflow for creating mining sub-identities:
# Start with master chain keychain -gen -name mining_master -store # Create mining identity keychain -genid -activate # Create backup mining identity keychain -genid -id 2 -store # Verify all identities keychain -show
Switching Between Identities
In Core:
# Switch to specific identity keychain -activate -id 2 # Verify active identity keychain -show # Switch back to primary keychain -activate -id 0
In Mobile:
- Open Settings
- Use identity toggle controls
- Verify address change
- Confirm with fingerprint
Identity Tracking and Organization
Create an identity management system:
- Document Structure:
Master Chain: mining_master ├── ID 0: Primary Mining (Active) ├── ID 1: Backup Mining ├── ID 2: Test Operations └── ID 3: Development
- Tracking Commands:
# Log all identities keychain -show > identity_log.txt # Track specific identity keychain -show -id 2 >> identity_log.txt
- Organization Tips:
- Keep a secure document mapping IDs to purposes
- Regular verification of active identities
- Clear naming conventions for each purpose
- Document all identity changes
Sample Identity Tracking Sheet:
Chain: mining_master Last Updated: [Date] ID 0: - Purpose: Primary Mining - Address: GRD... - Last Active: [Date] ID 1: - Purpose: Backup Mining - Address: GRD... - Last Active: [Date]